Working on NCS 1.5.1 and the factory bootloader here were my results:
Using the instructions here I set up my S3 bucket, etc.
Once set up I also updated
CONFIG_CLOUD_CLIENT_ID="feather-xxxx"
CONFIG_MQTT_BROKER_HOSTNAME="xxxx-ats.iot.us-east-1.amazonaws.com"
They seem to be the only things that need to be added to prj.conf
I downloaded the cert, private key and the Amazon Root CA1. Popped those in nRF Connect for Desktop and wrote them to the device.
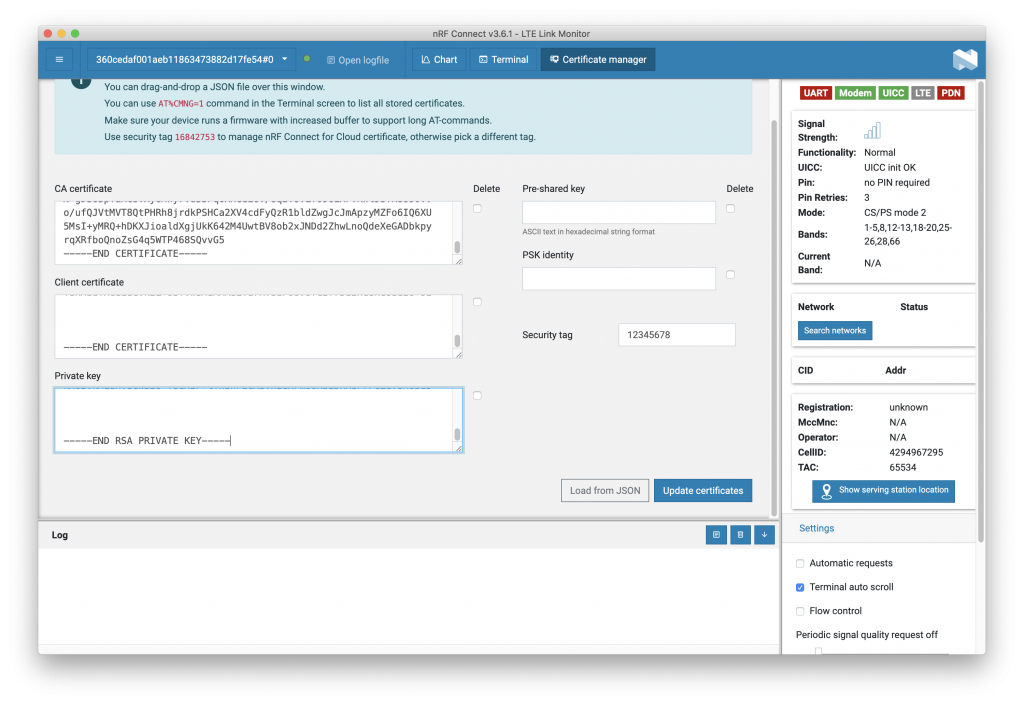
(I used the default security tag of 12345678)
Remember the device needs to be on but not connected (Using AT+CFUN=4 in order to add the certs.) Once complete setting AT+CFUN=0 is always a good idea.
A successful connection looks like:
2021-05-03T16:29:58.240Z DEBUG modem << MQTT AWS Jobs FOTA Sample, version: v1.0.0
2021-05-03T16:29:58.241Z DEBUG modem << Initializing modem library
2021-05-03T16:29:58.447Z DEBUG modem << Initialized modem library
2021-05-03T16:29:58.449Z DEBUG modem << LTE Link Connecting ...
2021-05-03T16:30:03.254Z DEBUG modem << LTE Link Connected!
2021-05-03T16:30:03.486Z DEBUG modem << IPv4 Address 3.224.183.138
2021-05-03T16:30:03.488Z DEBUG modem << client_id: feather-xxxxx
2021-05-03T16:30:08.503Z DEBUG modem << [mqtt_evt_handler:182] MQTT client connected!
2021-05-03T16:30:09.155Z DEBUG modem << [mqtt_evt_handler:235] PUBACK packet id: 17463
2021-05-03T16:30:09.216Z DEBUG modem << [mqtt_evt_handler:245] SUBACK packet id: 2114
2021-05-03T16:30:09.472Z DEBUG modem << [mqtt_evt_handler:235] PUBACK packet id: 20067
2021-05-03T16:31:10.994Z DEBUG modem << [mqtt_evt_handler:250] default: 9
2021-05-03T16:32:12.008Z DEBUG modem << [mqtt_evt_handler:250] default: 9
Then I created a job..
Running the update with the compiled bootloader works. While using the stock v2 bootloader does not work. Exactly as you were seeing @zirunhong. My earlier recommendation still stands considering the situation.